Security Vulnerability Remediation Pipeline Template
Handle vulns from alert to audit-ready closure
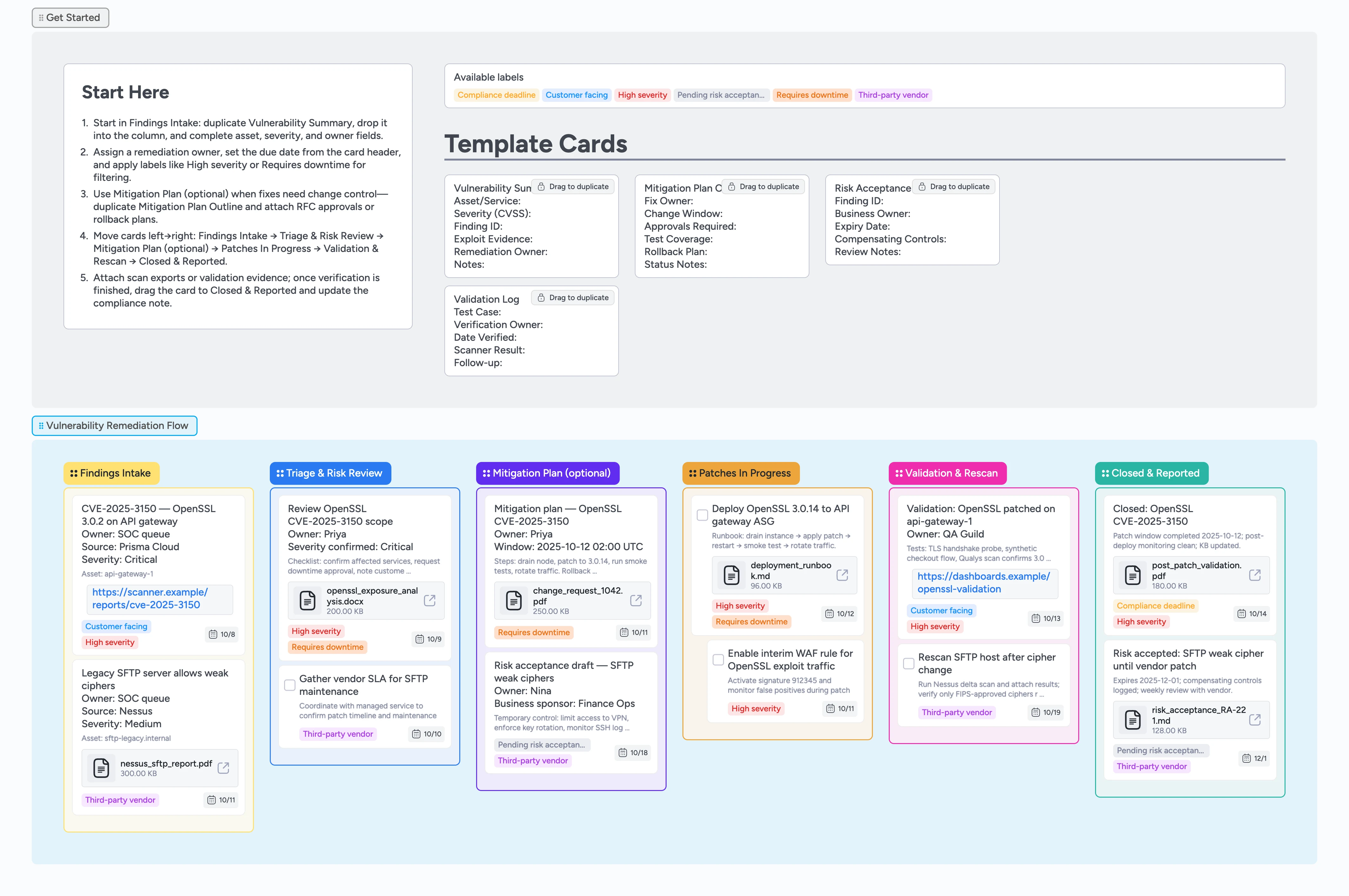
Security teams drown in alerts; this board turns them into an ordered flow. Duplicate the Vulnerability Summary card so every finding lands with asset, CVSS, and owner fields ready to assign. Apply labels to flag high severity, downtime, or vendor dependencies and triage in one place. Drag cards into the Mitigation Plan lane before patches kick off, attach change approvals, and line up due dates without swapping tools. By the time a card reaches Closed & Reported, validation evidence and audit notes are already captured.
- Pre-fill every finding with asset, CVSS, and owner by duplicating structured cards
- Highlight critical fixes using severity and downtime labels
- Coordinate change control with mitigation plan micro-templates
- Track remediation owners and due dates at a glance
- Attach validation PDFs and audit notes directly to cards
Start in Findings Intake — duplicate Vulnerability Summary
In the Vulnerability Remediation Flow, duplicate the Vulnerability Summary micro-template and drop it in Findings Intake. Fill Asset/Service, Severity, Finding ID, Exploit Evidence, and assign the remediation owner. Set the due date in the card header and apply labels like High severity or Third-party vendor so the right people notice it. Attach the latest scan export so investigators have proof.
Lead triage and confirm risk
Move the card to Triage & Risk Review once someone is calculating fix effort and downtime. Capture scope notes and downtime needs in the same card, or duplicate Mitigation Plan Outline if the change is complex. Tag Requires downtime and Compliance deadline when needed, and pull in vendor owners with card comments. Use due dates to reflect the SLA you committed to in triage without leaving the board.
Plan mitigations or log risk acceptance
When change control or business input is required, park the card in Mitigation Plan (optional). Duplicate Mitigation Plan Outline to list approvals, window, and rollback steps, attaching formal RFC files right on the card. If the business chooses not to fix immediately, duplicate Risk Acceptance Record, fill the expiry date, and tag Pending risk acceptance. Keep the card here until approvals are attached and the decision is documented.
Run remediation work with assignees and files
Drag the card into Patches In Progress once work starts. Convert fixes into task cards, keep owners assigned, and update due dates as the schedule shifts. Attach runbooks or scripts so engineers and security review the same record. Indent supporting tasks like interim WAF rules under the primary fix using the card indent control to show dependencies.
Validate, document, and close with evidence
After deployment, move to Validation & Rescan and duplicate Validation Log to record test cases and scanner results. Attach screenshots, scan files, or monitoring links as evidence. When everything passes, slide the card into Closed & Reported, update the compliance note in the description, and attach the final validation PDF. Clear urgent labels by clicking them off, but leave the history intact for future audits.
What’s inside
Six-stage remediation flow
Findings Intake, Triage & Risk Review, Mitigation Plan (optional), Patches In Progress, Validation & Rescan, Closed & Reported — move cards left-to-right as work advances so security leads spot bottlenecks fast.
Micro-templates for every decision
Vulnerability Summary, Mitigation Plan Outline, Risk Acceptance Record, and Validation Log cards are ready to duplicate so teams stop rewriting the same fields.
Severity-focused labels
High severity, Requires downtime, Third-party vendor, Pending risk acceptance, Compliance deadline, Customer facing — assign labels and filter work during standups.
Compliance-ready demos
Example cards include owners, due dates, labels, and attached files like change requests, runbooks, and validation PDFs, ready to duplicate so your team sees a complete record.
Risk acceptance lane
A dedicated optional stage keeps business sign-off, expiry dates, and compensating controls visible until the team can remediate.
Why this works
- Keeps every finding traceable from alert through closure because attachments, labels, and owner changes stay on the card
- Aligns security, engineering, and vendors on one timeline by giving everyone the same left-to-right view
- Captures approvals and validation evidence on the card for instant audit review
- Surfaces high-risk items fast with meaningful labels tied to severity and downtime
- Tracks risk acceptance decisions with clear expiry dates visible on the board
FAQ
Can we change the stage names?
Yes. Rename lists to match your change-control flow, but keep the left-to-right progression so cards show status at a glance.
How do we capture vendor-owned fixes?
Tag cards with Third-party vendor, assign the external owner in the card header or @-mention them in comments, and pin vendor attachments or SLAs directly to the card.
Where should scan results live?
Attach the Nessus, Qualys, or cloud scanner files to the card so analysts and auditors can find them without leaving the board.
What if we defer a vulnerability?
Duplicate Risk Acceptance Record, log the expiry date and compensating controls, tag Pending risk acceptance, and keep the card visible until the next review cycle.