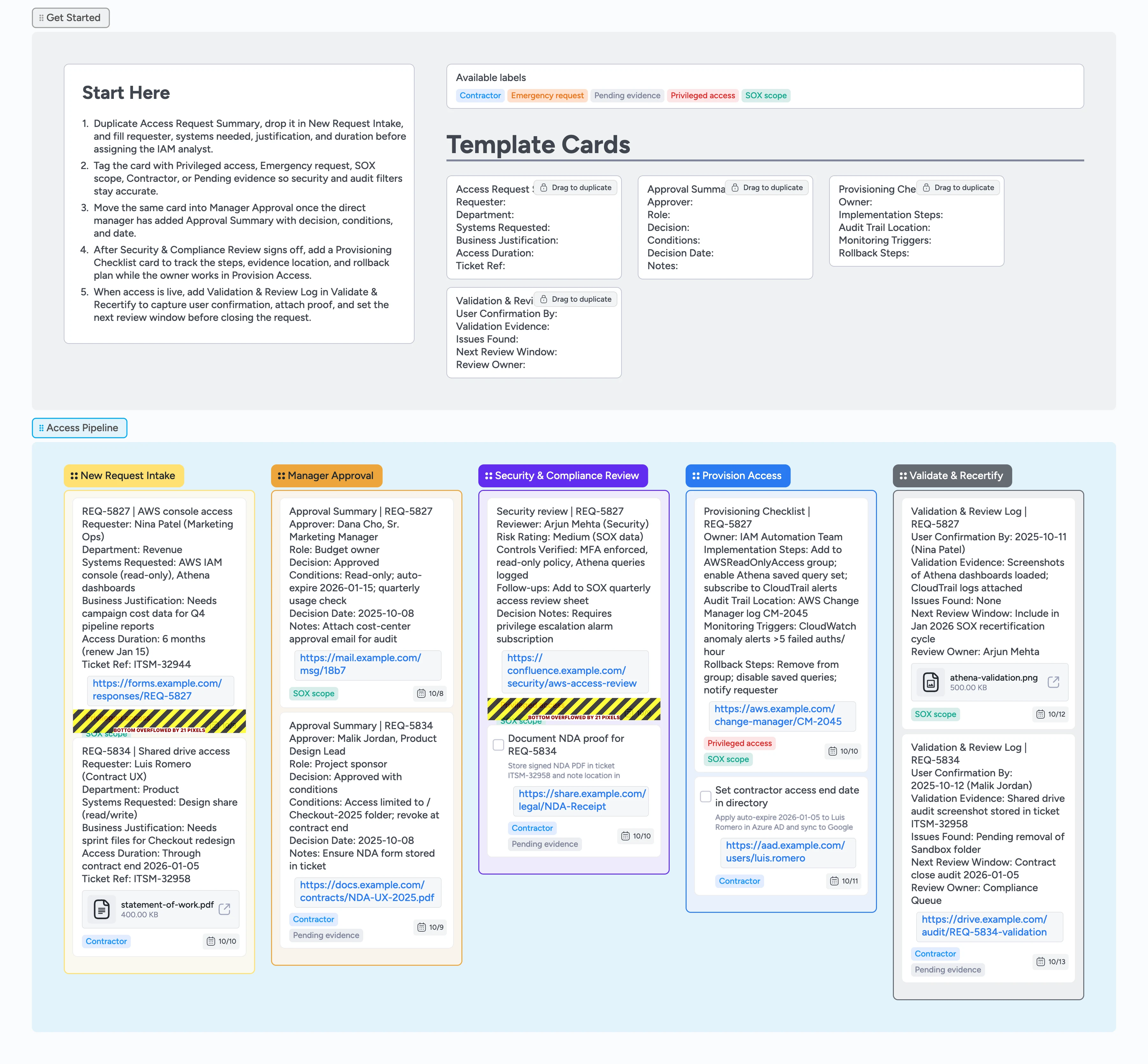
Access Requests Pipeline Template
Stop access approvals slipping through cracks
Requests scattered across email, tickets, and chat make auditors chase the trail and slow down provisioning. Instaboard lays out New Request Intake → Manager Approval → Security & Compliance Review → Provision Access → Validate & Recertify so one card flows through every gate. Duplicate the Start-Here cards to capture the requester’s business justification, move the same card through manager and security approvals, and add provisioning checklists once the team is ready to grant access. Labels flag privileged, emergency, and contractor scenarios so downstream owners know what requires extra scrutiny. When the user confirms success, the same card already holds attachments, checklists, and due dates, so your compliance team never has to chase screenshots.
- Watch cards move from Manager Approval to Provision Access in one live view and see teammates’ edits immediately
- Highlight privileged and emergency access with labels
- Attach approval emails, automation logs, and screenshots directly on the moving request card to keep the audit trail intact
- Schedule recertification checkpoints on the same card that stores provisioning logs so renewals stay tied to history
Kick off intake in New Request Intake
Duplicate Access Request Summary, drop it in New Request Intake, and fill requester, department, systems, justification, and access duration. Assign the IAM analyst who owns the request and set a due date for the intake SLA. Apply the right labels—Privileged access, Emergency request, SOX scope, Contractor, or Pending evidence—so downstream lists are pre-filtered. Attach the submitted form or statement of work immediately so approvers have context. The card you start here keeps every attachment and update as it moves left-to-right.
Secure manager approval before escalation
Slide the same card into Manager Approval once intake is complete. Duplicate Approval Summary, assign the manager, and record the decision date, conditions, and any required reminders. Add the approval email or chat transcript as an attachment so security reviewers see proof. Update labels if the manager flags anything that needs extra documentation.
Run security and compliance checks
Move the card into Security & Compliance Review for policy vetting. Open the request card and add checklist items for risk rating, control validation, and follow-up tasks, checking items off as controls clear. @mention the analyst in a card comment when evidence is missing so notifications stay inside Instaboard. Create task cards when security needs additional proof—the task inherits the labels and context so nobody digs through tickets—and keep Pending evidence tagged until files are uploaded. Adjust due dates to track required completion windows before provisioning.
Provision access and log the work
Drag the card into Provision Access and duplicate Provisioning Checklist to outline implementation steps, monitoring triggers, and rollback plans. Assign the engineer handling the change and attach automation logs or change tickets as they complete each step. Create task cards for supporting actions like scheduling auto-expiry or updating directories, keeping every subtask tied to the original request. Because the checklist lives on the same card that started intake, auditors can follow intake → approval → fulfillment without leaving the board. Once provisioning finishes, clear any open tasks so the lane stays focused on in-progress work.
Validate the grant and schedule recertification
Shift the card into Validate & Recertify and duplicate Validation & Review Log to capture user confirmation, validation screenshots, and the next audit window. Tag Pending evidence only if proof is outstanding, and clear it as soon as files land on the card. Set a follow-up due date for the next recertification cycle and add a task for offboarding reminders if the access should auto-expire—Instaboard notifications keep those deadlines visible. When everything is documented, move the card to your Closed row or apply a Done label so the pipeline stays clean.
What’s inside
Start-Here lane
Duplicate the Access Request Summary card from this lane to start every intake with required fields pre-formatted and labels ready.
Approval-ready micro templates
Preformatted Instaboard cards collect manager decisions, conditions, and dates so multi-level approvals live on the request itself before provisioning.
Provisioning checklist
Detail automation steps, rollback paths, and monitoring triggers on the same card as you fulfill the request.
Validation and recertification log
Capture user confirmation, attach screenshots, and set the next review window with a due-date task in one place.
Compliance-friendly labels
Privileged access, SOX scope, and emergency request tags let auditors click a label to filter the queue instantly.
Why this works
- Enforce multi-level approvals before provisioning
- Surface privileged and SOX-scoped work for faster review
- Keep provisioning logs and evidence tied to each request
- Schedule access recertification alongside completion tasks
FAQ
How should we handle urgent or emergency access?
Apply the Emergency request label, shorten the due date, and capture the expedited approval in the Approval Summary card so security reviewers can still verify controls before provisioning.
What evidence belongs on the card for audits?
Attach the original request form, manager sign-off, security review notes, automation logs, and validation screenshots so auditors can see the entire chain without leaving the board.
Can this pipeline cover contractors or short-term access?
Yes—use the Contractor label, add the end date inside the Access Request Summary card, and add removal tasks plus a recertification date in the Validation & Review Log.
How do we handle quarterly recertifications?
Keep the card in Validate & Recertify until you log the next review window and assign a task with the due date to whichever team owns access reviews—the task surfaces in their Instaboard notifications and calendar view.