DPA Reviews Pipeline Template
Run Every DPA Review On One Canvas
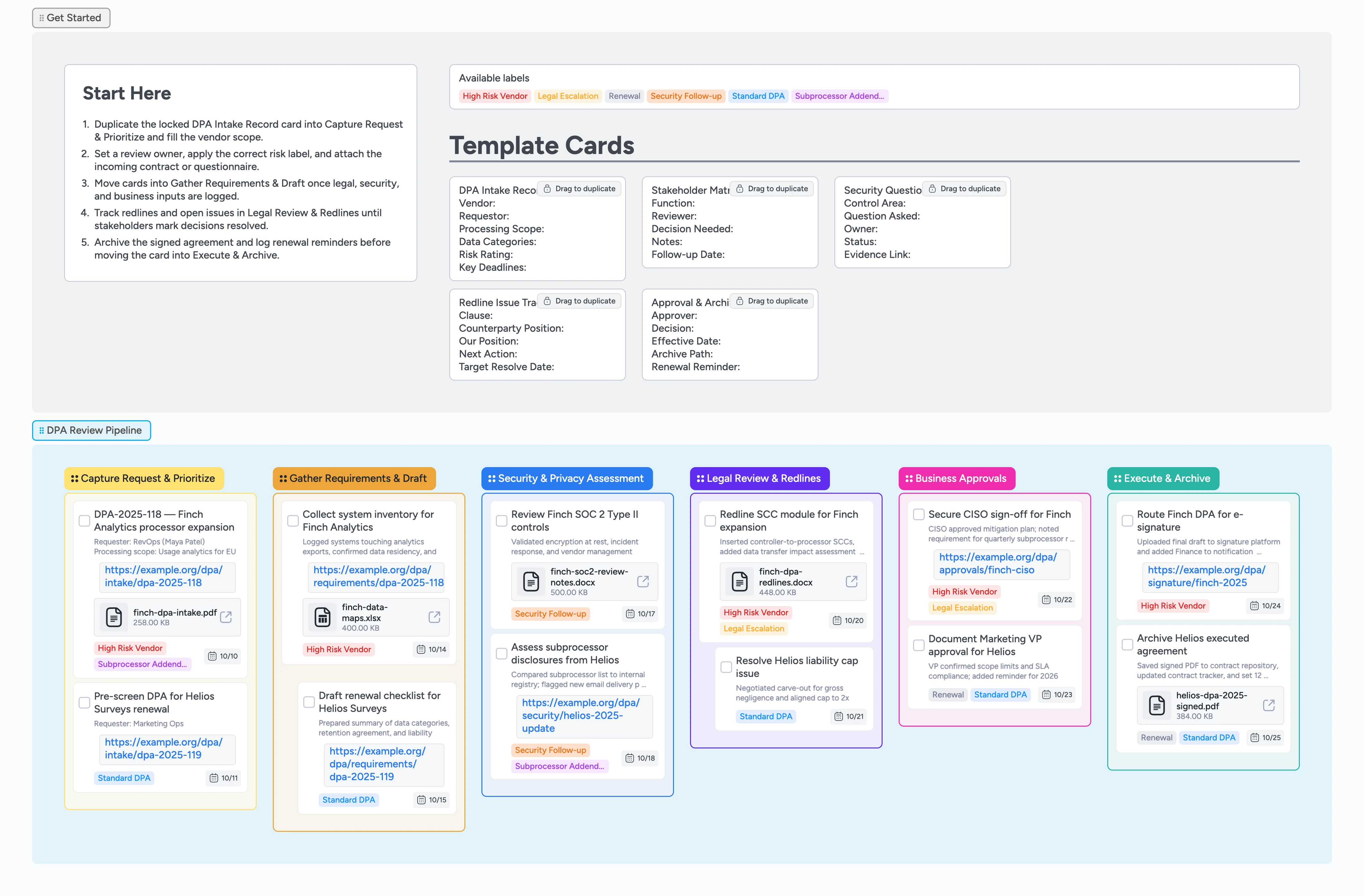
Missing a DPA renewal deadline because clauses live in scattered email threads can stall launches and force costly renegotiations. Vendor DPAs pile up across email threads, redline docs, and questionnaire portals, so this board keeps every agreement moving in one place. Duplicate the locked DPA Intake Record, drop it into Capture Request & Prioritize, and attach the incoming contract or security questionnaire so nothing slips. Labels like High Risk Vendor or Subprocessor Addendum flag escalations while due dates make statutory clocks obvious. As you gather requirements, route cards through Security & Privacy Assessment, collaborate on legal redlines, and log every approval comment directly on the card. When signatures land, archive the files and set renewal reminders without leaving the canvas.
- Prevent incomplete DPA intakes that delay downstream legal review
- Surface bottlenecks by moving cards left to right with owners and due dates
- Attach questionnaires, redlines, and approvals to keep evidence audit-ready
- Filter high-risk vendors instantly with labels for security or legal escalations
Capture the request and tag risk
Start in the Capture Request & Prioritize column, duplicate the locked "DPA Intake Record" card, and drop your copy into the list. Fill the vendor, processing scope, data categories, and deadlines so the team has a complete brief. Attach the incoming contract, questionnaire, or intake form to the card, assign the review owner, and set the due date that matches regulatory or launch timelines. Apply the High Risk Vendor, Standard DPA, or Subprocessor Addendum label to expose escalations instantly. Advance the card only after the intake fields, attachments, owner, and label are confirmed.
Draft the requirements brief
Move qualified cards into Gather Requirements & Draft and duplicate the Stakeholder Matrix micro-template so you can log every reviewer and decision needed. Capture subprocessors, system inventory, and timeline notes in the main card description, then attach supporting spreadsheets or questionnaires as you collect them so legal never re-asks for the list. Assign subject-matter owners on the in-card checklist, add short follow-up due dates, and indent supporting tasks under the parent card when you delegate research. Update labels if new risks appear so you can filter for High Risk Vendor or Legal Escalation during audits, and keep the card here until every input security and legal need is complete.
Complete security and privacy assessment
Drag the card into Security & Privacy Assessment once intake is ready, then duplicate the Security Questions Log template to capture each control topic. Record questionnaire responses, track mitigation tasks in the card checklist or nested sub-cards, and attach SOC reports or penetration summaries directly to the relevant entries. Apply the Security Follow-up label when owners owe fixes, assign them with concrete due dates, and filter that label across all DPAs to see every open item in one view. Use indentation to nest follow-up tasks under the primary assessment card, and only push to Legal Review & Redlines when outstanding security items are documented.
Pro tip: Filter by Security Follow-up to batch the gaps that still need remediation.
Run legal review and resolve redlines
In Legal Review & Redlines, duplicate the Redline Issue Tracker template for each clause that needs negotiation. Capture the counterparty position, your preferred language, and the next action so counsel can triage quickly. Tag sensitive items with Legal Escalation, assign the card to the attorney leading the negotiation, and attach redline docs or tracked changes to keep source files handy. Update statuses as responses arrive, add indentation for related sub-issues, and comment directly on the card so business stakeholders see the latest decision. When all blocking clauses close, move the parent card into Business Approvals.
Pro tip: Use labels plus indenting to separate must-have changes from nice-to-haves during review calls.
Secure approvals and archive the agreement
In Business Approvals, tag the CISO, finance partner, or business owner responsible for final sign-off and note any conditions in the card description. Duplicate the Approval & Archive Summary template to log who approved, when, and what needs future follow-up, then drag the card into Execute & Archive. Attach signed PDFs or e-sign links, paste the repository path, and set a renewal reminder date inside the card so the Renewal label stays actionable. Check off the task once the agreement is filed, and leave the card in Execute & Archive as your audit trail for auditors or procurement.
Pro tip: Set a repeating reminder by updating the due date after archiving so renewals surface in time.
What’s inside
Start-here intake lane
Duplicate-locked cards capture vendor, data scope, and deadlines before you assign an owner and set risk labels.
Requirements brief workspace
Use the Gather Requirements & Draft list to collect system inventories, subprocessors, and documents, attaching them to the primary card so downstream reviewers see full context without hunting through email.
Security questionnaire tracker
Security & Privacy Assessment cards log control findings, follow-up actions, and attachments such as SOC reports or penetration summaries.
Legal redlines lane
Legal Review & Redlines stores every clause decision, counterparty response, and next action so negotiations stay transparent.
Approvals and archive stage
Business Approvals and Execute & Archive capture stakeholder sign-off, signature status, and repository links with renewal reminders.
Why this works
- Aligns legal, security, and business reviewers around one shared pipeline
- Captures every decision, file, and deadline directly on the card history
- Highlights risky agreements with labels and due dates before they stall
- Keeps renewals visible by pairing completion with archive and reminder steps
FAQ
How should we handle security questionnaires and SOC reports?
Attach them directly to the cards in Security & Privacy Assessment and link to the evidence folder. That keeps every reviewer working from the same artifacts.
What if multiple teams review the same vendor?
Duplicate the Stakeholder Matrix template to log each function, assign tasks to their cards, and use labels like High Risk Vendor or Legal Escalation to flag handoffs.
Can we track renewals and recertifications?
Yes—apply the Renewal label, set a future due date on the card, and note the reminder in the Approval & Archive Summary so you know when to re-open the review.
Where do we log clause compromises or concessions?
Record them in the Redline Issue Tracker card: document the clause, the counterparty response, and your final position so future negotiations start from the latest precedent.