Privacy DSAR Requests Pipeline Template
Control Every DSAR Deadline in One Place
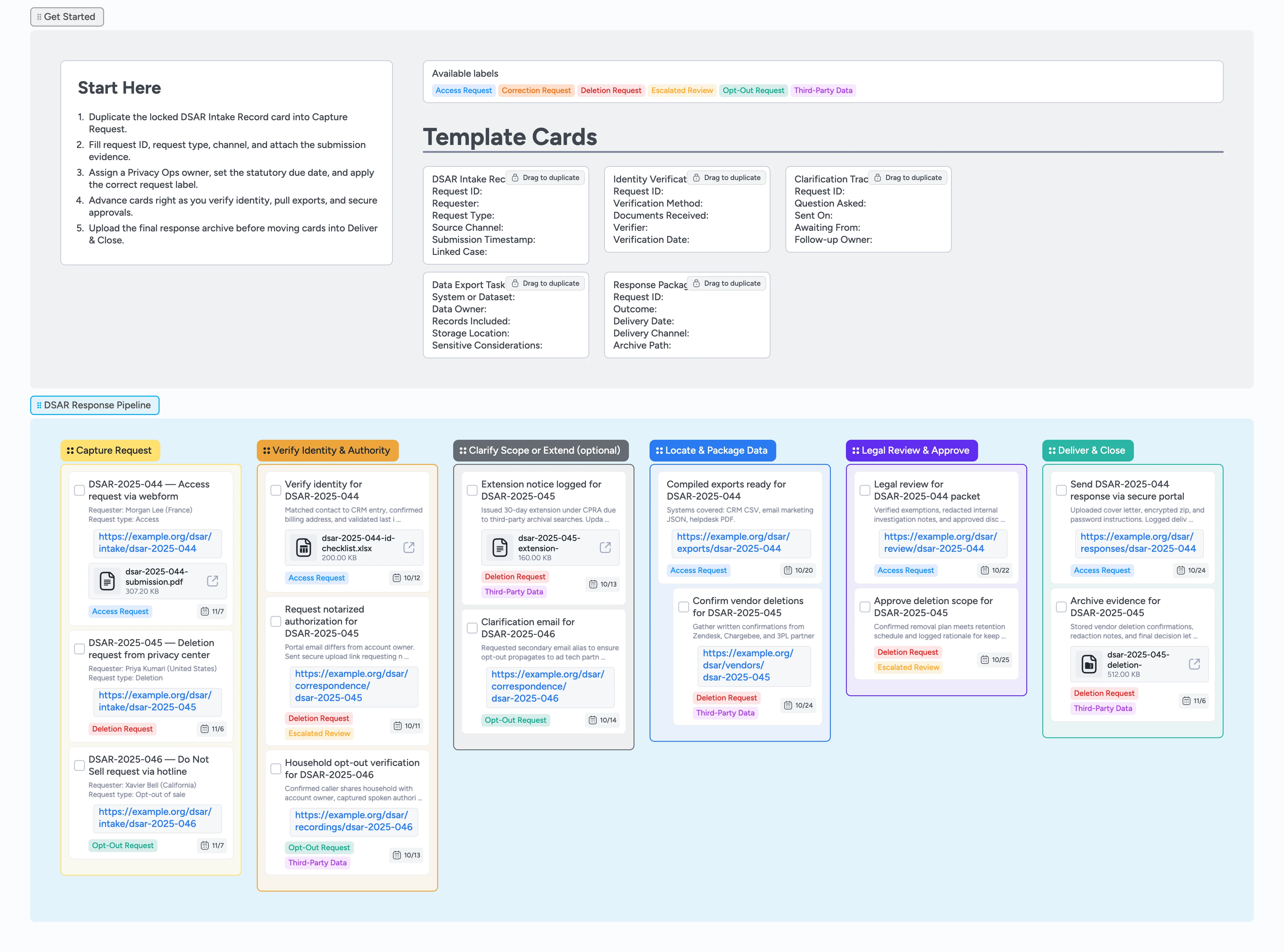
Privacy teams juggle intake emails, identity checks, and deletion proofs across too many tools, so this board maps the full DSAR lifecycle on one canvas. Duplicate the locked DSAR Intake Record card, drop it in Capture Request, and attach the original submission so compliance evidence never goes missing. Due dates and assignees surface statutory clocks while labels like Access Request or Third-Party Data flag nuanced handling. As you move cards through verification, data exports, legal review, and delivery, supporting documents, secure links, and extension letters stay pinned to each stage. The result: zero surprises when regulators ask for your log.
- Capture every DSAR intake with locked fields
- Expose SLA risk by dragging cards left to right and adjusting owners or extensions before deadlines
- Attach verification evidence and exports to each card
- Tag request types and escalations for instant triage
Log the request and start the clock
Begin in the Capture Request list, duplicate the locked "DSAR Intake Record" card, and drop your copy into the pipeline. Fill the request ID, request type, channel, and submission timestamp fields so the legal team shares one source of truth. Attach the original form submission or ticket export to preserve evidence. Assign the card to the Privacy Ops owner managing the case, set the due date that reflects the statutory deadline, and add the label that matches the request type. Move the card forward only after intake details, attachments, and ownership look complete.
Finish identity verification fast
Open the card in the Verify Identity & Authority column and use the locked template to log how you validated the requester. Upload ID checklists, notarized letters, or call recordings directly to the card so they stay linked to the audit trail. Tag escalations with the "Escalated Review" label if legal must weigh in before you proceed. When verification passes, mark the checkbox task complete, update the due date if the timeline shifts, and advance the card to the next list.
Manage clarifications and extensions
Route cards into Clarify Scope or Extend (optional) whenever you need more data from the requester or must pause the clock. Duplicate the Clarification Tracker micro-template to record the question asked, the outbound date, and who owes a reply. Attach extension letters or follow-up emails so they are ready for auditors. Apply the "Third-Party Data" label whenever external vendors are involved so you can filter those cards and batch follow-ups, and set a short follow-up due date so holding patterns do not get lost.
Pro tip: Keep one card per requester active so every extension stays tied to their original DSAR ID.
Collect exports without losing track
In Locate & Package Data, duplicate the Data Export Task template for each system you must query. Assign the card to the system owner, list the records included, and link to the secure folder where you dropped the export. Use indentation to nest vendor confirmations or additional purge subtasks beneath the primary card. Attach zip files, spreadsheets, or proof screenshots as you receive them so nothing is trapped in email. Update due dates to reflect scheduled vendor responses before you hand off to legal review.
Secure approvals and deliver
Move ready cards into Legal Review & Approve and tag counsel or privacy leadership to capture sign-off in the comment thread. Record exemption decisions in the description so approvers and auditors can see why data was withheld, keep deletion scope notes updated, and use labels like "Escalated Review" whenever exceptions warrant extra scrutiny. After legal okays the package, drag the card to Deliver & Close, upload the cover letter and encrypted export, and log the delivery confirmation ID. Archive evidence files on the card so you can prove completion years later, then mark the checkbox to close the request.
What’s inside
Start-Here intake lane
Duplicate-locked cards capture request ID, channel, and submission evidence so intake never leaves gaps before you set the statutory due date.
Identity and authority checkpoint
Verify authority with a dedicated list for ID proofs, notarized permissions, and call recordings so you can demonstrate compliance instantly.
Data discovery workspace
Track exports, vendor confirmations, and retention notes with due dates, attachments, and indentation so you can nest vendor tasks under the parent export card and keep complex deletion paths visible.
Legal approval lane
Use comment threads for counsel sign-off, log exemption decisions on the card, and apply Escalated Review labels so approvals stay inside the lane.
Delivery archive
Log secure delivery, cover letters, and archived evidence on Deliver & Close cards so attachments and confirmation IDs stay ready for audits.
Why this works
- Centralizes intake, verification, discovery, approval, and delivery on one canvas
- Surfaces regulatory deadlines with visible due dates and left-to-right movement so teams can reassign owners or request extensions before they slip
- Creates consistent records through reusable micro-templates and locked fields
- Keeps audit evidence beside every decision so compliance questions are easy to answer
FAQ
What if DSARs arrive through multiple channels?
Duplicate the intake template for every new request, note the channel in the Source field, and attach the original submission so you can prove timing no matter where it came in.
How do we reference our ticketing or CRM IDs?
Log the external case number inside the Linked Case line on the intake card and paste a deep link under attachments. That keeps your system of record connected while Instaboard drives execution.
Can we separate opt-out, correction, and deletion requests?
Yes—apply the built-in labels for Access, Deletion, Correction, or Opt-Out requests. Filter by label when you need to review workload or create reports for regulators.
Where should we store photo IDs and sensitive proofs?
Attach them directly to the verification cards and lock the shared drive link so access is restricted. Once the DSAR closes, edit the card to remove the ID file, add a comment with the archive link, and leave a note pointing to the long-term evidence location.