Patch Rollout Pipeline Template
Run patch rollouts as a repeatable pipeline
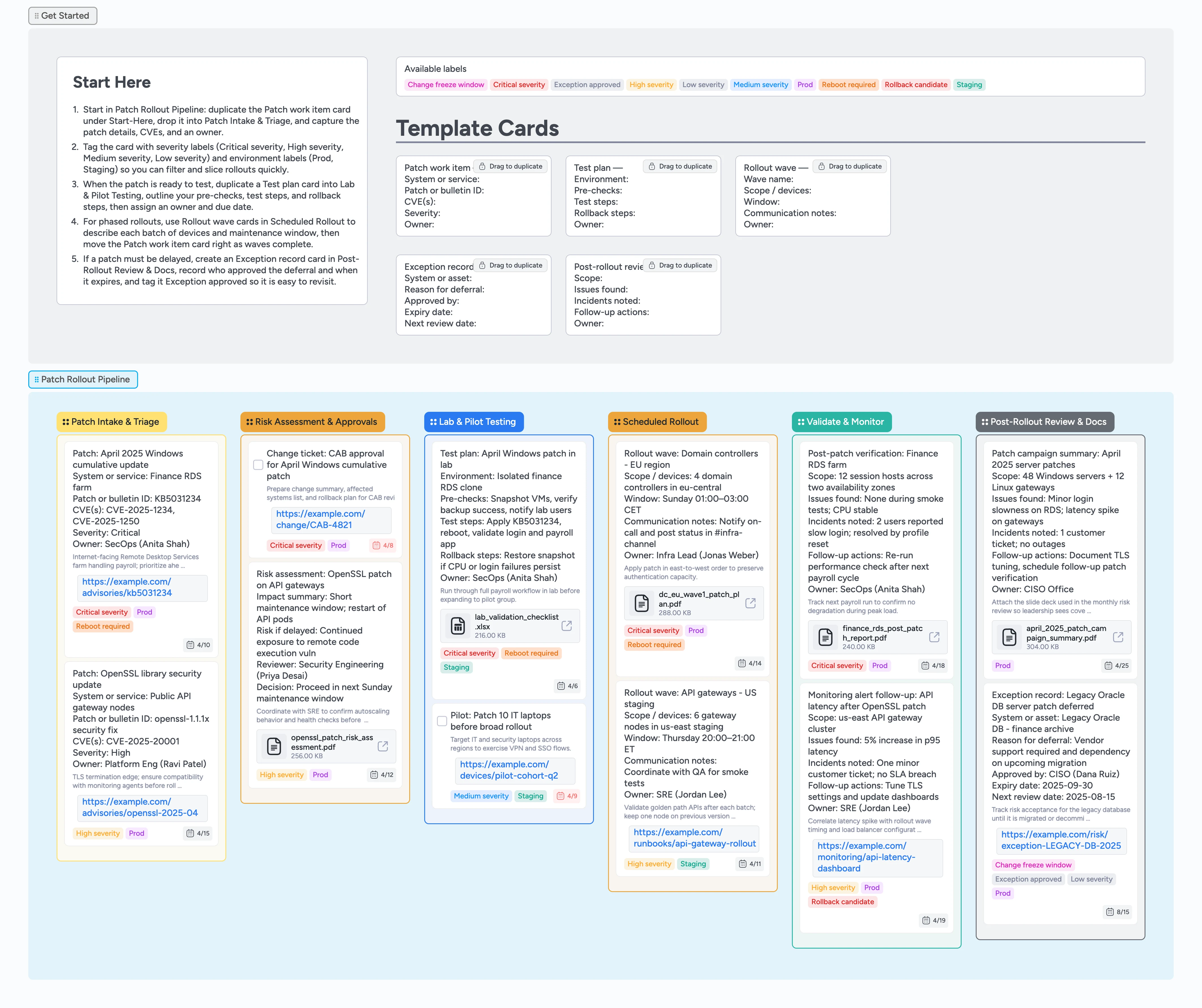
Instead of chasing patch work across tickets, spreadsheets, and change calendars, this template gives you a single patch rollout board where you duplicate a patch card and drag it through six stages. Each card represents a patch or patch campaign that moves left-to-right from Patch Intake & Triage through Post-Rollout Review & Docs, keeping CVEs, owners, approvals, and rollout notes together. Duplicate micro-template cards for patch work items, test plans, rollout waves, and exception records so every change follows the same structure. Labels highlight severity and environment, while due dates and assignees keep maintenance windows clear. Attach test reports, monitoring screenshots, and risk acceptance documents directly to cards so audits and follow-ups are easy.
- Drag patch cards through six stages from intake to post-rollout
- Track risk, owners, and approvals on reusable patch cards
- Use labels and due dates to prioritize critical fixes
- Attach test plans, reports, and exception docs to cards
- Duplicate wave and test plan templates for each rollout
Capture your first patch in Patch Intake & Triage
Open the board and start in the Getting Started area above the Patch Rollout Pipeline section, where you will see the Patch work item micro-template card. Duplicate that card, drop it into the Patch Intake & Triage list, and rename it for the patch or patch campaign you need to ship next. Fill in the system or service, patch or bulletin ID, CVEs, severity, and owner fields so the card becomes the home for that change. Apply severity labels such as Critical severity or High severity plus environment labels like Prod or Staging so you can filter later. Assign yourself or a teammate and set a due date to anchor the rollout on your calendar.
Pro tip: Rename the board with your team or environment name so the patch pipeline feels like your own space.
Assess risk and secure approvals in Risk Assessment & Approvals
Once the basics are captured, drag the patch card into the Risk Assessment & Approvals stage so everyone can see it is under review. On that same patch card, add a short risk assessment section in the description to summarize potential impact, blast radius, and rollback approach, then attach links or files from your ticketing system or change advisory board. Tag high-risk patches with Critical severity or High severity so they stand out during review. Capture who approved the change and any conditions directly on the card so decisions are easy to reference later. When approvals are in place, move the card right into Lab & Pilot Testing.
Design lab tests and pilots in Lab & Pilot Testing
In Lab & Pilot Testing, duplicate the Test plan card from the Getting Started area to outline how you will validate the patch, or, if you need a special case, create a custom card on this list instead. List your pre-checks, test steps, and rollback steps directly on the card so the team can follow the same script each time. Use tags like Staging and Reboot required to make disruptive tests easy to spot. Attach lab validation checklists, screenshots, or reports so passing tests are documented for future rollouts. When a pilot cohort is ready, add a task card describing the pilot devices and move the main patch card to Scheduled Rollout.
Plan rollout waves and track live deployment
In Scheduled Rollout, use Rollout wave cards to define each batch of servers, endpoints, or services you will update. Duplicate the Rollout wave micro-template for every wave, filling in scope, window, communication notes, and owner so handoffs are clear. Apply labels like Prod, Staging, and Reboot required so you can scan for risky changes at a glance. As rollout windows start, update the patch work item card with notes or checklists and move it across the stage when waves finish. If issues appear, tag the card Rollback candidate and pause the rollout while you investigate in Validate & Monitor.
Validate, monitor, and log exceptions
After each wave completes, move the patch card into Validate & Monitor and duplicate the Post-rollout review micro-template card into that stage to record what you tested, incidents you saw, and follow-up actions. Use the attachment button to add monitoring dashboards, export reports, or screenshots to those cards so audit and incident reviews have concrete evidence. When a patch must be deferred, duplicate the Exception record micro-template and drop it into the Post-Rollout Review & Docs list, describe the system and reason for deferral, and note who approved it. Tag these cards Exception approved and any relevant severity labels and set a due date so they do not get lost among completed work. Use the summary cards in this final stage to prepare leadership updates and schedule the next patch campaign.
What’s inside
Six-stage patch rollout pipeline
Patch Intake & Triage, Risk Assessment & Approvals, Lab & Pilot Testing, Scheduled Rollout, Validate & Monitor, and Post-Rollout Review & Docs keep each patch moving left-to-right from idea to closed-out change, and you drag cards across stages so status is always visible.
Reusable patch work item templates
Patch work item, Test plan, Rollout wave, Exception record, and Post-rollout review cards give you structured fields for scope, CVEs, risk, rollback steps, and follow-up actions, and you duplicate these pre-built cards for every campaign instead of starting from scratch.
Severity and environment labels
Labels like Critical severity, High severity, Medium severity, Low severity, Prod, and Staging make it easy to filter for risky changes or specific environments when planning and reporting, and to prioritize what you see during live rollout windows.
Test plan and rollout wave cards
Dedicated cards for lab validation and rollout waves help you define pre-checks, test steps, windows, and communication notes so pilots and production waves follow the same playbook.
Exception and post-rollout review lane
The final stage captures summary reports and exception records so deferrals, risk acceptances, and lessons learned stay visible long after a patch finishes rolling out.
Why this works
- Turns scattered patch tickets and spreadsheets into one visible pipeline
- Keeps risk, approvals, and rollout details on the same card
- Makes lab tests, rollout waves, and rollback plans easy to reuse
- Surfaces exceptions and deferrals so they are not forgotten
- Creates an audit-friendly history of patch campaigns with attached evidence
FAQ
Can I use this template if we already have a ticketing or patching tool?
Yes. Keep raising and tracking changes in your ticketing or patch management platform, then paste ticket URLs into the patch work item card description or attach the tickets as files or links so Instaboard becomes the visual hub for planning, rollouts, and exceptions.
What kinds of patches does this template work for?
The pipeline is flexible enough for operating system updates, endpoint agents, infrastructure patches, firmware, and SaaS security updates. Treat each card as a patch or campaign and use labels to distinguish environments or platforms.
How should I use this with a change advisory board (CAB)?
Use the Risk Assessment & Approvals stage to prepare and document CAB decisions. Attach meeting notes or approval tickets to the card, capture conditions or freeze windows in the description, and move the card forward only after approvals are recorded. Add an Approved label or check off an approval task on the card so it is obvious when CAB sign-off is complete.
Does this replace our CMDB or asset inventory?
No. Your CMDB or asset inventory remains the source of truth for systems and ownership. The template sits on top as a rollout workspace that ties systems, risk decisions, and patch status together for each campaign. Reference CMDB asset IDs or hostnames in the patch card's System or service field so you can cross-check scope during rollout.