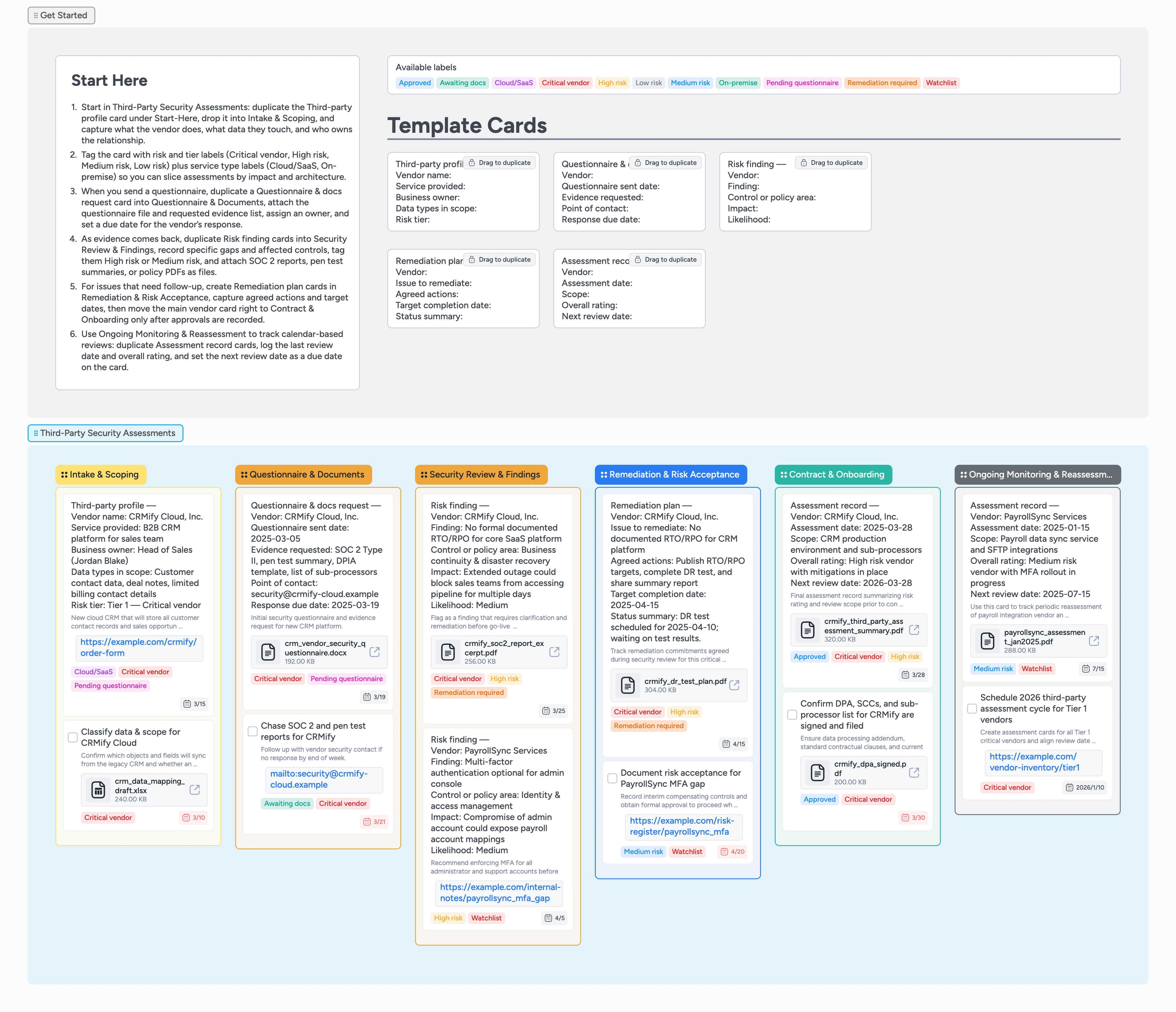
Third-Party Security Assessments Pipeline Template
Keep every vendor security review on track
Instead of chasing third-party assessments across spreadsheets, tickets, and email, run the whole process on one visual board. This template gives security, risk, and legal a shared pipeline to log new vendors, send questionnaires, collect evidence, score findings, and record approvals. Duplicate reusable cards for vendor profiles, evidence requests, and risk findings so every assessment starts the same way. Attach SOC 2 reports or pen test summaries directly to cards, then move each vendor left-to-right until onboarding and monitoring are complete, with a clear trail you can show auditors during compliance reviews.
- Centralize vendor evidence, findings, and approvals on one board
- Highlight critical vendors and high-risk findings with labels
- Standardize questionnaires and remediation plans with micro-templates
- Keep renewal and reassessment dates visible with due dates
- Help security, legal, and procurement collaborate in real time with comments and card-level threads
Log a new vendor in Intake & Scoping
Welcome the team by opening the Get Started section and duplicating the Third-party profile card so every vendor starts with the same checklist. Drop the duplicate into the Intake & Scoping list and fill in vendor name, service description, data types in scope, business owner, and risk tier. Assign the card to the internal owner so accountability is obvious. Set a due date for the initial assessment window so it appears in your calendar views. Apply labels like Critical vendor, Cloud/SaaS, or On-premise to make filtering by impact and architecture easy.
Pro tip: Start with your most critical in-flight vendors so you see value from the pipeline immediately.
Send questionnaires and request evidence
When you are ready to kick off due diligence, duplicate the Questionnaire & docs request card and move it, along with the vendor card, into the Questionnaire & Documents stage. Fill in the questionnaire sent date, evidence requested, and vendor contact details so everyone knows what is outstanding. Attach the actual questionnaire file or link it from your GRC tool using the card attachments. Set a response due date and tag the card Pending questionnaire or Awaiting docs so blockers are visible at a glance. Use comments on the card to log email chases so the full history stays in one searchable thread instead of buried in individual inboxes.
Review evidence and capture risk findings
Once SOC reports and policy documents arrive, move the vendor into Security Review & Findings. Duplicate Risk finding cards for each issue you identify and fill in the control area, impact, and likelihood so later reviewers can understand the context quickly. Apply High risk or Medium risk labels on both the vendor card and individual findings so critical gaps stand out. Attach supporting files like report excerpts or internal notes directly to the finding cards. Assign each finding to a reviewer and use due dates to keep the assessment on schedule.
Pro tip: Keep one finding per card so remediation owners and conversations stay focused.
Drive remediation, approvals, and ongoing monitoring
For issues that need follow-up, slide vendor and finding cards into Remediation & Risk Acceptance and duplicate a Remediation plan card to track agreed actions. Fill in the issue, specific remediation steps, target completion date, and a short status summary, then assign the card to the vendor owner or control owner. When risks are addressed or formally accepted, move the vendor into Contract & Onboarding and use an Assessment record card to summarize the rating, scope, and next review date, attaching approval emails or signed DPAs as files. Finally, park the vendor in Ongoing Monitoring & Reassessment, duplicate an Assessment record card for the next cycle, and set a due date so recurring reviews never slip—and because due dates surface on the board, overdue reassessments are visible to the whole team, not just the card owner.
What’s inside
Six-stage assessment pipeline
Intake & Scoping through Ongoing Monitoring & Reassessment keeps every vendor moving from first contact to long-term oversight.
Third-party profile cards
Capture service scope, data types, business owner, and risk tier in a duplicate-ready profile card for each vendor.
Questionnaire and evidence tracker
Log questionnaires sent, documents requested, and follow-ups so SOC 2, pen tests, and DPAs never get lost in email threads, and filter by labels like Pending questionnaire or Awaiting docs so you only chase true blockers.
Risk findings and remediation lane
Record specific control gaps, tag them High risk or Medium risk, and attach remediation plans with target dates and owners.
Assessment records and monitoring
Use Assessment record cards to document overall rating, scope, and next review date so monitoring and renewals stay predictable.
Why this works
- Creates a repeatable path from vendor intake to long-term monitoring by moving the same vendor card through each stage
- Keeps questionnaires, evidence, findings, and approvals tied to one vendor card so context and history are never scattered across tools
- Surfaces critical vendors and high-risk findings with simple labels so risk hotspots are obvious during reviews and standups
- Makes remediation and risk acceptance decisions auditable at a glance because approvals, comments, and attachments live on the same cards
- Aligns security, legal, and procurement around the same live pipeline instead of separate spreadsheets and inbox threads
FAQ
Can I use this for existing vendors?
Yes. Duplicate Third-party profile cards for vendors you already work with, drop them straight into Security Review & Findings or Remediation & Risk Acceptance, and tag Annual review so they enter your monitoring cycle.
Where should I store confidential reports?
Keep SOC reports, pen tests, and contracts in your secure repository, then attach links or redacted files to the cards. The board tracks status, reminders, and decisions without exposing sensitive documents broadly, and keeps a clear audit trail of who reviewed which documents and when.
How do I adapt stages to our process?
You can rename stages, add labels, or tweak micro-templates while keeping the left-to-right flow. The key is that every vendor card moves from intake through questionnaire, review, remediation, and ongoing monitoring.
What if a vendor refuses remediation?
Leave their cards in Remediation & Risk Acceptance, tag the findings High risk and Watchlist, and create a task card for formal risk acceptance so leadership can decide whether to approve, limit scope, or exit the vendor.