Threat Modeling Requests Pipeline Template
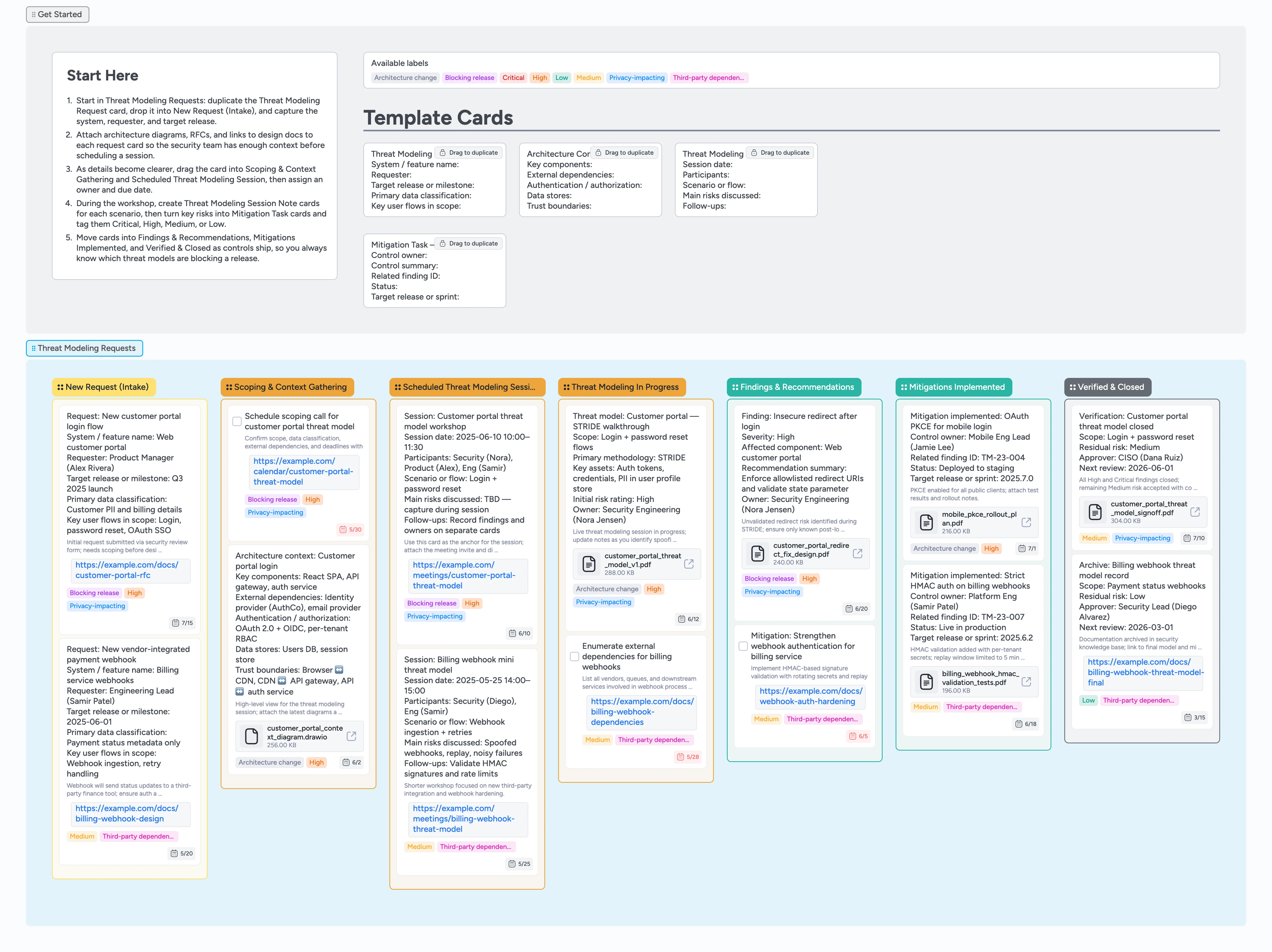
1) Capture your first request in New Request (Intake) • 2) Gather architecture context in Scoping & Context Gathering • 3) Schedule and run workshops in Scheduled Threat Modeling Session • 4) Turn findings into mitigation work in Findings & Recommendations • 5) Track implementation and close out in Mitigations Implemented and Verified & Closed
Make threat modeling requests audit-ready and visible
Security and engineering teams often juggle threat modeling requests in forms, chats, and tickets, making it hard to see what is in scope, what is blocking a release, and what still needs sign-off for audits. This template gives you one board where each card represents a request that flows from intake through scoping, workshops, findings, mitigations, and final approval. Right from the Getting Started area you duplicate structured micro-template cards for requests, architecture context, session notes, and mitigation tasks so every review follows the same checklist. Labels show risk and impact, while assignees and due dates keep reviews aligned to sprint or release milestones. Attach diagrams, RFCs, and reports directly to cards so a single click reveals the full history behind each threat model.
- Centralize threat modeling intake, scoping, and sign-off
- Track every request’s progress from intake through verified closure
- Surface risky or blocking changes with security-specific labels
- Attach diagrams, RFCs, and reports directly to request cards
- Ensure every team follows the same threat modeling checklist
Capture your first request in New Request (Intake)
Open the board and start in the Getting Started area above the Threat Modeling Requests section, where you will see the Threat Modeling Request micro-template card. Duplicate that card, drop it into the New Request (Intake) list, and rename it for the system or feature you need to review. Fill in the requester, target release or milestone, primary data classification, and key flows in scope so the card becomes the single home for that request. Attach architecture diagrams, RFCs, or design docs and apply labels such as Critical, High, or Privacy-impacting so risk is obvious at a glance. Assign yourself or a teammate and set a due date aligned to the release so the review does not slip.
Pro tip: Use the description field on the request card to paste links to tickets or docs your team already relies on.
Gather architecture context in Scoping & Context Gathering
Once intake is captured, drag the request card into the Scoping & Context Gathering list so it is clear you are clarifying details. In the Getting Started area, duplicate the Architecture Context micro-template card and drop it next to the request to capture components, external dependencies, authentication, data stores, and trust boundaries. Attach or link to diagrams and note any vendors or upstream systems, then apply labels like Third-party dependency or Architecture change where they apply. Assign a security owner and set a due date on the context card so preparation work does not stall. When the picture looks complete, update the request card’s due date to the planned workshop date and move it into Scheduled Threat Modeling Session.
Schedule and run workshops in Scheduled Threat Modeling Session
In the Scheduled Threat Modeling Session stage, duplicate a Threat Modeling Session Note card for each workshop you plan. Use the fields on that card to record the session date, participants, scenario or flow, and the main risks you expect to explore. Attach the calendar invite, Instaboard board link, or diagrams so stakeholders can join and follow along easily. During the workshop, add checklists or comments to the Session Note card as you walk through STRIDE or your preferred method, then drag it into Threat Modeling In Progress so the board reflects active analysis. For every major risk you identify, create or duplicate a findings card in Findings & Recommendations so follow-up work is clearly separated from raw meeting notes.
Turn findings into mitigation work in Findings & Recommendations
In the Findings & Recommendations stage, create one card per significant risk so you can track status independently from the workshop. Use the card title and description to describe the issue, severity, affected components, and recommended control, or start from a Mitigation Task micro-template card for structure. Apply labels such as Critical, High, Medium, Low, Blocking release, or Privacy-impacting so the riskiest issues stand out. Attach screenshots, reports, or code snippets that support the finding so engineering can act without hunting for context. Assign owners and set due dates so mitigation work surfaces on team calendars instead of getting stuck as a note in a document.
Track implementation and close out in Mitigations Implemented and Verified & Closed
As fixes ship, move mitigation cards into the Mitigations Implemented stage and keep the Mitigation Task fields updated with status and target release information. Attach test reports, rollout notes, or links to pull requests so each control has concrete evidence behind it and the finding card shows the full story in one place. When verification is complete, drag the main request card into Verified & Closed and create or duplicate a sign-off card that captures residual risk, approver, and next review date, using the example cards in that column as a guide. Adjust labels to reflect residual risk, for example switching from Critical to Medium or Low as mitigations land and removing Blocking release when the issue is no longer gating launch. Over time, this final column becomes an audit-ready history of threat modeling decisions you can open in a single click during reviews.
What’s inside
Clear pipeline from intake to verified closure
New Request (Intake), Scoping & Context Gathering, Scheduled Threat Modeling Session, Threat Modeling In Progress, Findings & Recommendations, Mitigations Implemented, and Verified & Closed keep each request moving left-to-right from first intake through documented sign-off.
Request and context micro-templates
Threat Modeling Request and Architecture Context cards capture system details, requester, target release, data classification, and trust boundaries so every workshop starts with the same information.
Session notes separated from actionable findings
Threat Modeling Session Note cards help you log methodology, scenarios, and risks discussed in each workshop while separate findings and mitigation cards capture the specific issues that need owners and deadlines.
Mitigation task tracking
Mitigation Task cards turn findings into work items with clear owners, status, and target release or sprint fields so mitigations do not get lost between teams.
Risk and dependency labels
Labels like Critical, High, Medium, Low, Blocking release, Privacy-impacting, Third-party dependency, and Architecture change make it easy to scan and filter for the riskiest or most blocking requests.
Why this works
- Turns scattered threat modeling asks into one visible queue
- Keeps requests, workshops, findings, and mitigations on linked cards
- Aligns reviews with release timelines using labels, owners, and due dates
- Creates a repeatable path from request through sign-off
- Leaves an audit-ready trail of risk decisions and supporting evidence
FAQ
Do I need a formal threat modeling framework to use this template?
No. The pipeline works whether you use STRIDE, PASTA, or a simple checklist; each card becomes the home for scope, status, risks, and mitigations even if detailed models or diagrams live in Confluence, Notion, or another repository.
How does this template work with Jira or other ticketing tools?
Keep creating tickets in your existing tools, then paste links into request or mitigation cards and attach relevant artifacts so Instaboard acts as the visual hub for scope, status, and sign-off.
Can non-security teams submit threat modeling requests directly?
Yes. Share the board with product and engineering, ask them to duplicate the Threat Modeling Request micro-template in New Request (Intake), and let the security team own the downstream scoping, workshop, and mitigation stages.
Can I adapt this for privacy or compliance reviews?
You can reuse the same intake, context, workshop, findings, and sign-off pattern for privacy impact assessments or control reviews by adjusting labels and copy while keeping the pipeline structure intact.