Vendor Risk Reviews Pipeline Template
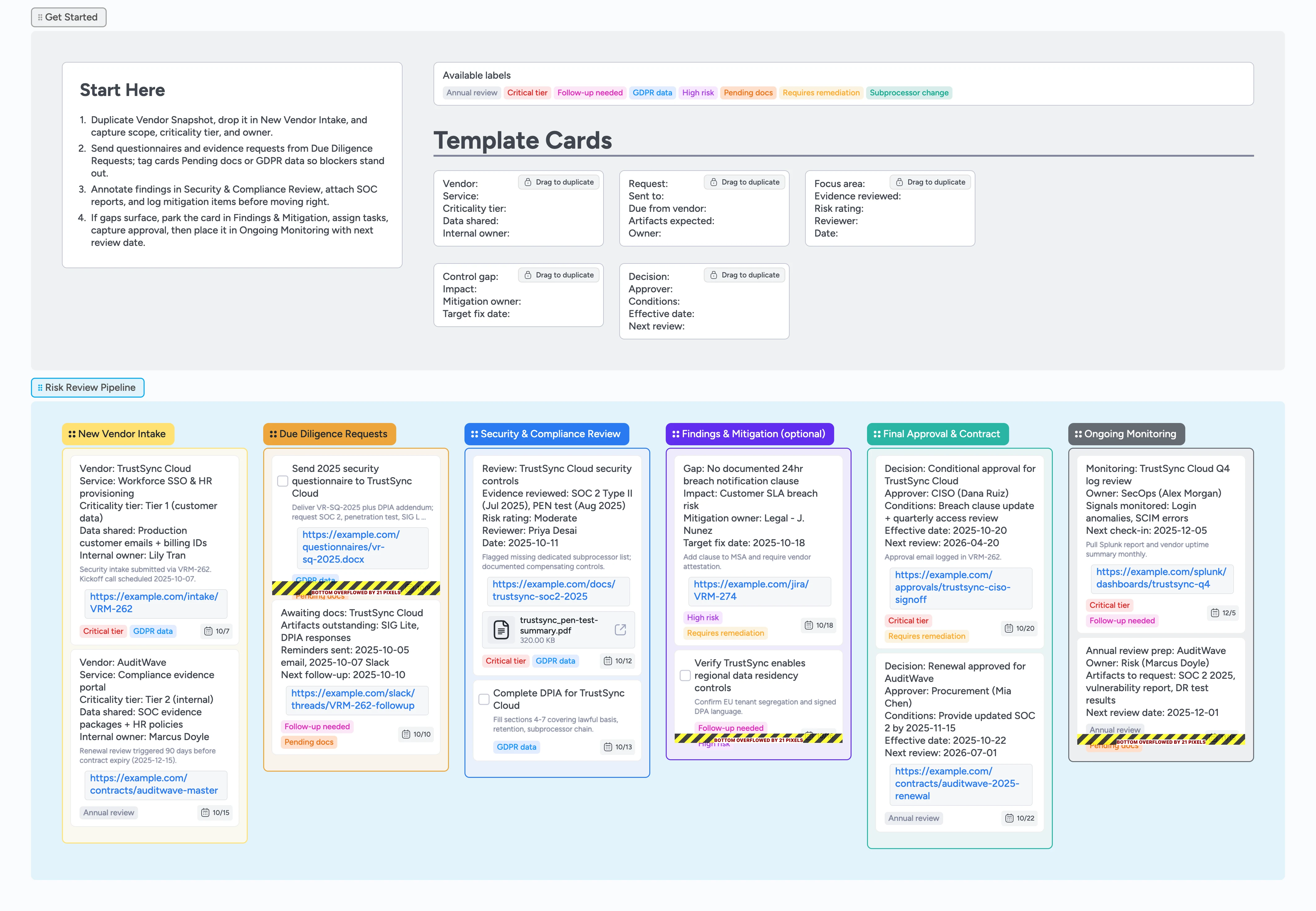
Run vendor risk reviews from one hub
Turn spreadsheets and email chases into a single workflow. This template gives security, legal, and procurement one board to log vendor intake, send due diligence packets, review evidence, and document sign-off. Duplicate reusable cards for questionnaires, risk findings, and approvals so every vendor starts with the same checklist, then slide each vendor left-to-right as work finishes. Labels highlight critical vendors and missing artifacts, while due dates keep mitigation deadlines in sight. Finish by parking each supplier in Ongoing Monitoring with the next review date already set.
- Centralize attachments, approvals, and mitigation history on each vendor card
- Expose high-risk vendors with labels and due dates
- Hand off remediation tasks with duplicate-ready cards
- Keep monitoring checkpoints visible after onboarding
Log a vendor in New Vendor Intake
Welcome the team by opening the Get Started section and duplicating the Vendor Snapshot card so every vendor starts with the same checklist. Drop it into the New Vendor Intake list and fill vendor name, service scope, criticality tier, data shared, and internal owner. Set a due date for the initial review window so it surfaces on the board. Apply the Critical tier or GDPR data labels if the vendor touches customer or personal data.
Kick off due diligence requests
Duplicate the Request card for each questionnaire or evidence packet you need. Move the vendor card into Due Diligence Requests once outreach is sent so the stage reflects active work. Attach the latest SOC 2, SIG, or DPIA files directly to the card. Tag blockers with Pending docs or Follow-up needed and set reminder due dates to keep the vendor accountable.
Run the security and compliance review
Slide the card into Security & Compliance Review when documents arrive. Use the Focus area template to note which controls you evaluated, attach the reports in the card attachments, and set the Risk rating field or apply the High risk label when needed. Assign reviewers on the card so ownership is explicit. If you uncover issues, duplicate the Control gap template as its own card and move both into Findings & Mitigation for remediation.
Approve, contract, and schedule monitoring
After mitigations finish, move the vendor into Final Approval & Contract. Capture the decision, approver, conditions, and next review date with the Decision micro template. Attach the signed MSA or approval email so audit evidence lives alongside the card. Finally drop the vendor into Ongoing Monitoring, duplicate the monitoring checklist card, and set a due date 6–12 months out so the next review stays visible.
What’s inside
Six-stage pipeline
New Vendor Intake through Ongoing Monitoring keeps due diligence, approvals, and recurring reviews moving left-to-right.
Reusable vendor snapshot cards
Capture service scope, data shared, criticality tier, and internal owner in one duplicate-ready micro template.
Due diligence request tracker
Log questionnaires sent, evidence collected, and reminder dates so nothing slips between email threads.
Findings and mitigation lane
Record control gaps, assign mitigation owners, and set fix-by deadlines before approvals move forward.
Monitoring playbook
Duplicate the monitoring checklist card annually, set due dates, and track log review notes inline to stay compliant year round.
Why this works
- Creates a repeatable path from intake to approval
- Flags high-risk vendors before they reach production
- Tracks remediation owners and deadlines in one place
- Locks in future reviews so monitoring is never forgotten
FAQ
How do I store confidential evidence?
Keep files in your secure repository and paste the link into the card attachments or description. The board tracks status and reminders without exposing sensitive documents.
Can I adapt this for existing vendors?
Yes. Duplicate the Vendor Snapshot card for each active supplier, drop cards straight into Security & Compliance Review, and tag Annual review to show it is part of the re-certification cycle.
What if a vendor skips remediation?
Leave the card in Findings & Mitigation, tag it High risk and Requires remediation, and create a task card assigned to the owner so leadership can escalate before approving.